
I. Introduction
The rise of fraud calls and its impact on individuals
Understanding different types of fraud calls
In today’s digital age, fraud calls have become a common nuisance that can have a significant impact on individuals. These calls often come from scammers and fraudsters who aim to deceive innocent people and gain access to their personal information or money. The rise of such calls has led to an increased need for individuals to protect themselves and stop potential fraud calls.
Understanding the different types of fraud calls is crucial in tackling the issue effectively. Here are some common types of fraud calls:
- Impersonation Calls: Scammers pretend to be representatives from well-known organizations or government agencies, such as banks, the IRS, or tech support. They often use scare tactics to trick individuals into providing personal information or making payments.
- Robocalls: Robocalls are automated calls that deliver pre-recorded messages. Fraudsters use robocalls to reach a large number of targets and trick them into revealing sensitive information or making financial transactions.
- Phishing Calls: Phishing calls involve scammers pretending to be from reputable companies, such as financial institutions or online platforms. They attempt to obtain personal information, such as login credentials or credit card details, by making individuals believe there is an urgent issue with their account.
- Social Engineering Calls: Fraudsters use social engineering tactics to manipulate individuals into providing personal information willingly. They may create a sense of urgency, offer fake rewards or threaten consequences to deceive their victims.
It is essential to stay informed about the different types of fraud calls and be aware of the red flags that indicate a potential scam. Taking proactive measures and learning how to stop potential fraud calls can help individuals protect themselves from falling victim to these scams.
II. Caller ID Spoofing
What is caller ID spoofing and how does it work?
Caller ID spoofing is a technique used by scammers and fraudsters to manipulate the caller ID display on your phone, making it appear as if the call is coming from a trusted source, such as a bank, government agency, or a familiar number. This can trick individuals into answering the call and sharing personal information, falling victim to scams or identity theft.
Caller ID spoofing works by using Voice over IP (VoIP) technology or other methods to alter the caller ID information that is transmitted with the call. The scammer typically replaces their actual phone number with a different number, which can be a local number, a well-known company’s number, or even a number that matches the area code and prefix of your own phone number.
Methods to identify and block spoofed calls
While it may be challenging to completely stop all potential fraud calls, there are some steps you can take to identify and block spoofed calls:
1. Avoid answering unknown or suspicious calls: If you receive a call from an unknown number or a number that you find suspicious, it’s best to let it go to voicemail. Legitimate callers will often leave a message, while fraudsters may not.
2. Do not share personal information over the phone: Avoid providing sensitive information, such as your Social Security number, bank account details, or credit card information, over the phone unless you initiated the call and are certain of the recipient’s identity.
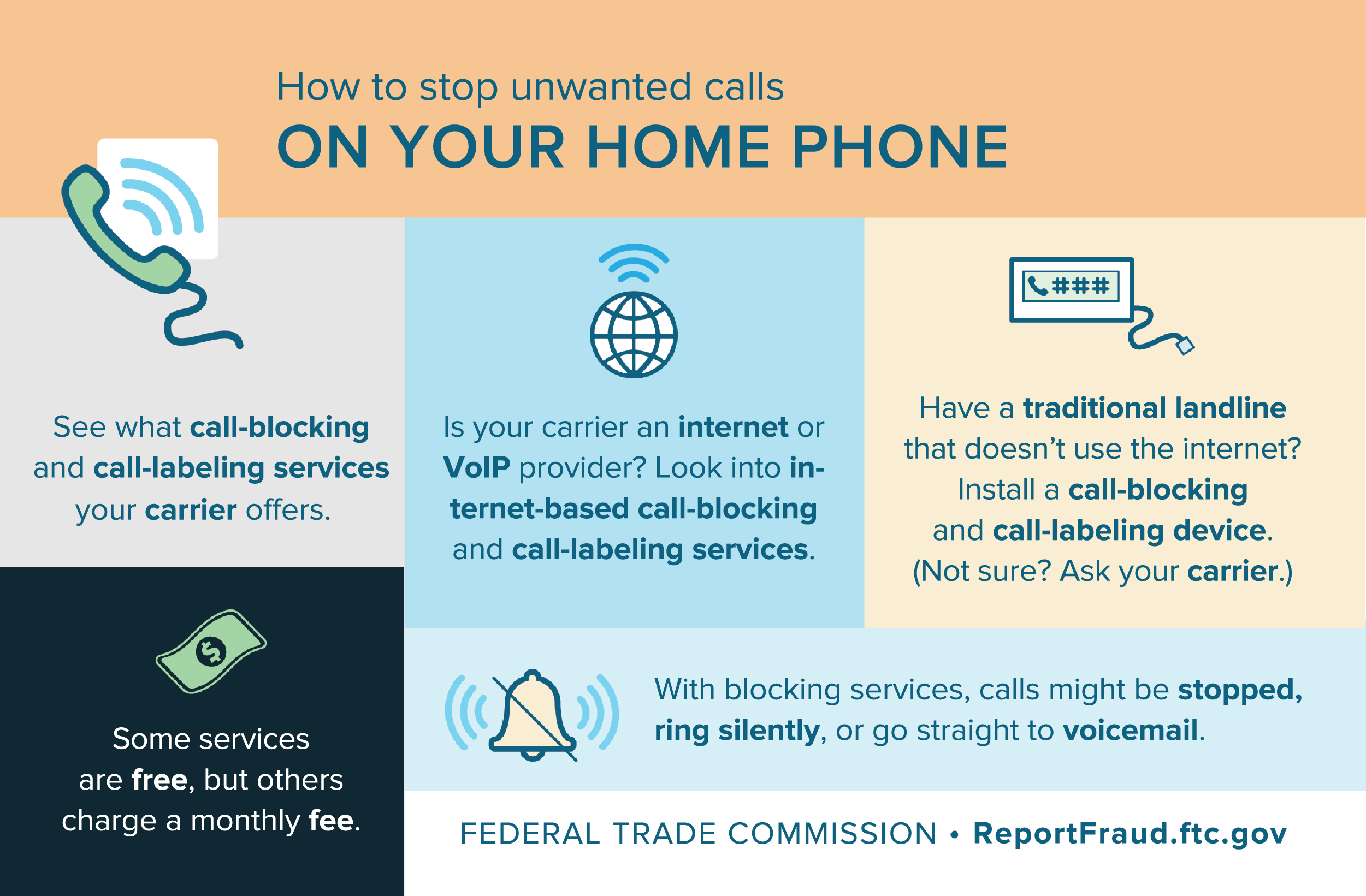
3. Use call-blocking services or apps: Many phone carriers offer call-blocking services or apps that can help identify and block spoofed calls. These services can automatically screen or block calls from known scam numbers or those reported by other users.
4. Install a call-blocking app: There are various call-blocking apps available for both iPhone and Android devices that can help identify and block suspicious calls. These apps often use crowd-sourced data and algorithms to analyze incoming calls and determine their likelihood of being fraudulent.
5. Report spoofed calls: If you receive a spoofed call, report it to your phone carrier and the appropriate authorities. Your report can help authorities investigate and take action against scammers and fraudsters.
Remember, scammers are constantly evolving their tactics, so it’s important to stay vigilant and skeptical of unknown or suspicious calls. By taking steps to identify and block spoofed calls, you can help protect yourself from potential fraud.

III. Robocalls and Automated Scams
Understanding robocalls and automated scams
Robocalls and automated scams have become a prevalent issue for many individuals, causing annoyance and potential financial harm. Here’s a brief overview of what they are and how they work:
- Robocalls: Robocalls are automated telephone calls that deliver pre-recorded messages to a large number of recipients simultaneously. They are often used for telemarketing purposes or to spread scams and fraudulent schemes.
- Automated scams: Automated scams involve fraudulent individuals or organizations using robocalls to trick people into sharing personal information or making payments. These scams can range from fake lottery winnings and debt collection threats to IRS impersonation and tech support scams.
Tips to prevent and block robocalls
Dealing with robocalls can be frustrating, but there are several steps you can take to prevent and block them:
- Register your number: Add your phone number to the National Do Not Call Registry in your country. This will help reduce calls from legitimate telemarketers.
- Be cautious: Be wary of giving out your phone number on websites, social media platforms, or any other online platforms, as it increases the chances of receiving unwanted calls.
- Don’t answer unknown calls: If you receive a call from an unknown number, let it go to voicemail. Legitimate callers will leave a message.
- Block unwanted numbers: Most smartphones have built-in features that allow you to block specific phone numbers. Take advantage of this feature to block persistent robocalls.
- Use call-blocking apps: Install call-blocking apps on your smartphone to automatically identify and block known spam and robocalls.
- Report unwanted calls: If you continue to receive unwanted robocalls, report them to the appropriate authorities in your country. This helps in tracking and taking action against scammers.
By following these tips, you can reduce the number of robocalls you receive and protect yourself from falling victim to automated scams.
IV. Phishing Calls and Social Engineering
Identifying phishing calls and social engineering techniques
Phishing calls and social engineering techniques are common tactics used by fraudsters to deceive individuals and gain access to their personal information. Here are some ways to identify phishing calls and social engineering techniques:
1. Unsolicited calls: Be cautious of unsolicited calls from unknown numbers. Fraudsters often pose as representatives from banks, government agencies, or well-known companies to gain your trust.
2. Urgency and threats: Scammers may create a sense of urgency and use threats to pressure you into providing personal information or making immediate payments. Be wary of high-pressure tactics.
3. Suspicious requests for personal information: Legitimate organizations will never ask you to provide sensitive information like social security numbers, passwords, or credit card details over the phone. If someone asks for this information, it’s likely a scam.
4. Caller ID spoofing: Fraudsters may use technology to manipulate caller ID to make it appear as if the call is coming from a trusted organization. Don’t solely rely on caller ID for verification.
5. Poor grammar and pronunciation: Phishing calls often come from scammers who may not speak English fluently or use poor grammar. Pay attention to these signs as they can indicate a scam call.
Steps to avoid falling victim to phishing scams
Taking the following steps can help protect you from falling victim to phishing scams:
1. Be cautious: Always be skeptical of unfamiliar calls, especially those asking for personal information. It’s better to be cautious and hang up rather than provide sensitive information to potential scammers.
2. Verify the caller: If you receive a call from someone claiming to be from a legitimate organization, hang up and call back using a trusted phone number. This ensures you are speaking to a genuine representative.
3. Don’t disclose personal information: Never share personal or financial information over the phone unless you initiated the call and know you are speaking to a trustworthy source.
4. Update your security software: Keep your devices and security software up to date to protect against phishing attacks and other online threats.
5. Educate yourself: Learn about common phishing techniques and how to identify them. Stay informed about the latest scams and share this information with your friends and family.
By following these steps, you can minimize the risk of falling victim to phishing calls and social engineering scams. Remember, it’s always better to err on the side of caution and protect your personal information.

V. Government and Financial Institution Impersonation Calls
Recognizing government and financial institution impersonation calls
Government and financial institution impersonation calls are a common tactic used by scammers to gain access to personal information and commit fraud. It is important to be able to recognize these calls to protect yourself and your financial security. Here are some tips to help you identify potential fraud calls:
1. Stay vigilant: Be cautious of any unexpected calls claiming to be from government agencies or financial institutions. Scammers often use high-pressure tactics to create a sense of urgency and panic.
2. Verify the caller’s identity: Government agencies and financial institutions will never ask for your personal information, such as your Social Security number or bank account details, over the phone. If a caller requests this information, it is a red flag.
3. Hang up and call back: If you receive a suspicious call, hang up and call the official number of the government agency or financial institution directly. Use a trusted source, such as their official website or phone directory, to find the correct contact information.
4. Be wary of threats and demands: Scammers often use threats of legal action or demands for immediate payment to intimidate victims. Remember that government agencies and financial institutions will never request payment over the phone or threaten you with arrest.
5. Report suspicious calls: If you receive a fraudulent call, report it to your local authorities and the Federal Trade Commission (FTC). Providing them with information can help with investigations and prevent others from falling victim to scams.
Being aware of these tactics and remaining vigilant can help protect you from falling victim to government and financial institution impersonation calls. Always prioritize your personal and financial security by verifying the identity of callers and reporting any suspicious activity.
For more information on identifying and preventing fraud calls, visit the FTC’s website. Stay informed, stay safe.
VI. Recognizing Tech Support Scams
Indications of tech support scams and how they operate
Tech support scams have become increasingly common, with scammers targeting individuals and tricking them into providing access to their computers or personal information. Here are some indications of tech support scams and how they operate:
1. Unsolicited phone calls: Tech support scammers often make unsolicited phone calls, claiming to be from renowned tech companies like Microsoft or Apple. They may inform you that your computer has been compromised and offer to fix the issue remotely.
2. Alarmist messages: Scammers may display alarming pop-up messages on your computer, stating that it is infected with viruses or malware. These messages are often designed to create a sense of urgency and prompt you to take immediate action.
3. Request for remote access: Tech support scammers may ask you to grant them remote access to your computer, allowing them to control it remotely. This gives them the opportunity to install malicious software or steal sensitive information.
4. Payment requests: Scammers may request payment for their services, claiming that they have resolved the issue on your computer. They may ask for payment via credit card or request your banking details.
It’s important to be aware of these indications and exercise caution when encountering tech support calls or messages.
Preventive measures to avoid becoming a victim
To protect yourself from falling victim to tech support scams, here are some preventive measures to consider:
1. Be skeptical of unsolicited calls: If you receive an unsolicited phone call from someone claiming to be from a tech company, it’s best to be skeptical. Legitimate tech support companies will not call you out of the blue.
2. Hang up and verify: If you suspect a call to be a scam, hang up without providing any personal information. You can independently verify the legitimacy of the call by contacting the tech company directly through their official website or customer support line.
3. Update software and use security tools: Keeping your operating system and security software up to date can help protect against potential vulnerabilities that scammers may exploit. Enable firewalls and use reputable antivirus software.
4. Educate yourself: Familiarize yourself with common tech support scams and stay informed about the latest tactics used by scammers. This knowledge will help you recognize and avoid potential scams.
5. Be cautious with remote access: Only grant remote access to your computer if you have initiated the request and are confident in the legitimacy of the service provider. Never grant access to someone who contacts you unsolicited.
By staying vigilant and following these preventive measures, you can reduce the risk of falling victim to tech support scams. Remember, it’s always better to err on the side of caution when it comes to your personal information and computer security.
VII. Do Not Call Registry and Call Blocking Apps
Utilizing the National Do Not Call Registry
One effective way to mitigate potential fraud calls is by adding your phone number to the National Do Not Call Registry. This is a free service provided by the Federal Trade Commission (FTC) that allows you to opt out of receiving telemarketing calls from legitimate companies. By registering your number, you can reduce the number of unwanted calls you receive, including those from potential fraudsters. It is important to note that the registry does not apply to political calls, charitable organizations, or calls from companies with which you have an existing business relationship.
Overview of call blocking apps and their effectiveness
Call blocking apps can be used as an additional layer of protection against potential fraud calls. These apps work by identifying and blocking known spam and fraudulent numbers. Some call blocking apps also allow you to create a personal block list, where you can add specific numbers that you want to block. Additionally, they may offer features like call filtering or screening, which can help identify potential fraud calls before you even answer them.
While call blocking apps can be effective in reducing the number of unwanted calls you receive, it is important to choose a reputable app that is regularly updated with the latest fraud numbers. Popular call blocking apps include Truecaller, Hiya, and Nomorobo. These apps are available for both Android and iOS devices and offer a range of features to help protect you from potential fraud calls.
By utilizing the National Do Not Call Registry and installing a call blocking app, you can take proactive steps to reduce the number of potential fraud calls you receive and protect yourself from falling victim to phone scams.

VIII. Reporting Fraud Calls
The importance of reporting fraud calls
Reporting fraud calls is essential in the fight against scammers and protecting yourself and others from falling victim to their schemes. By reporting these calls, you help authorities track down the culprits and raise awareness about different types of scams. Additionally, reporting fraud calls can help prevent future scams and protect vulnerable individuals in your community.
Here are a few reasons why reporting fraud calls is crucial:
- Preventing financial losses: Reporting fraud calls can help prevent others from losing their hard-earned money to scammers, as authorities can take action to shut down fraudulent operations.
- Identifying trends and patterns: By reporting fraud calls, law enforcement agencies can identify trends and patterns in scam activities, which can inform their efforts to prevent fraud and educate the public.
- Building a case against scammers: Reporting fraud calls provides authorities with valuable evidence that can be used to build a case against scammers and increase the likelihood of prosecution.
Contacting the relevant authorities for reporting scams
If you receive a fraudulent call, it’s important to report it promptly to the appropriate authorities. Here are some steps you can take:
- Federal Trade Commission (FTC): File a complaint with the FTC through their website or by calling their toll-free hotline at 1-877-FTC-HELP (1-877-382-4357). The FTC’s Complaint Assistant allows you to provide details about the fraud call and helps law enforcement agencies identify and track down scammers.
- Local law enforcement: Contact your local police department or sheriff’s office to report the fraud call. They may ask for additional information or direct you to the appropriate agency to handle the complaint.
- Your phone service provider: Inform your phone service provider about the fraudulent call. They may have specific protocols or procedures to handle such incidents.
Remember to provide as much information as possible when reporting fraud calls, including the phone number, date and time of the call, and any details about the scam or the caller’s tactics. This information can assist authorities in their investigations and efforts to combat fraud.
Reporting fraud calls is a crucial step in protecting yourself and others from falling victim to scams. By taking action, you can contribute to the fight against fraud and help create a safer environment for everyone.
IX. Protecting Personal Information
How to safeguard your personal information from fraudulent callers
Protecting your personal information is crucial in preventing fraud calls. Here are some tips to help you safeguard your information and avoid falling victim to fraudulent callers:
- Be cautious with sharing information: Be wary of sharing personal information, such as your social security number, bank account details, or passwords, over the phone. Most legitimate organizations will not ask for this sensitive information over a phone call.
- Caller ID verification: Fraudsters may use a technique called spoofing to manipulate their caller IDs, making it appear as if they are calling from a reputable organization. Don’t solely rely on caller ID to verify the authenticity of the caller.
- Do not trust unsolicited calls: If you receive an unsolicited call from someone claiming to be from a bank, government agency, or any other organization, be skeptical. Hang up and independently verify the caller’s identity by calling the organization’s official customer service number.
- Use a call-blocking app: Install a reputable call-blocking app on your smartphone. These apps can identify and block spam and fraudulent calls automatically.
- Register on the Do Not Call Registry: In many countries, including the United States, you can register your phone number on the National Do Not Call Registry to reduce the number of telemarketing calls you receive. This won’t eliminate fraudulent calls entirely, but it can help reduce their frequency.
Taking these precautions can help protect your personal information and minimize the risk of falling victim to fraud callers. Remember, it’s essential to remain vigilant and skeptical when receiving calls from unknown numbers.
X. Caller Verification and Trusted Contacts
Verifying callers and establishing trusted contacts
One effective way to stop potential fraud calls is by implementing caller verification and establishing a list of trusted contacts. Here are some steps you can take to achieve this:
1. Caller ID: Most smartphones and landline phones have caller ID features. Make sure to enable this feature so that you can see the name and number of incoming calls. If the caller ID displays an unknown or suspicious number, you can choose not to answer the call.
2. Screening Calls: Consider using call screening services or apps that provide additional information about the caller. Some apps automatically screen and block known scam numbers, providing an extra layer of protection.
3. Two-Way Authentication: In some cases, you may receive calls from legitimate organizations or individuals. To verify their identity, consider implementing a two-way authentication process. This can involve asking security questions, requesting a callback from a known and trusted number, or using additional verification steps.
4. Trusted Contacts: Maintain a list of trusted contacts, such as family members, close friends, or important service providers. These are individuals or organizations whose calls you would always answer. By establishing a list of trusted contacts, you can prioritize answering their calls while being cautious with unknown numbers.
Implementing additional layers of security
In addition to caller verification and trusted contacts, there are other steps you can take to enhance your phone’s security and prevent potential fraud calls:
1. Do Not Call Registry: Register your phone number with the official Do Not Call Registry in your country. This can help reduce the number of unwanted telemarketing calls you receive.
2. Call Blocking: Many smartphones offer call blocking features that allow you to block specific numbers or even whole categories of calls, such as international calls or private numbers.
3. Be Cautious with Personal Information: Avoid sharing sensitive personal information, such as your social security number or bank account details, over the phone unless you initiated the call and are certain of the caller’s identity.
4. Report Fraudulent Calls: If you receive a suspicious call, report it to your local authorities or the appropriate authority in your country. Providing information about fraud calls can help in tracking down scammers and preventing others from falling victim to their schemes.
By implementing these caller verification and security measures, you can significantly reduce the risk of potential fraud calls and protect yourself from
XI. Conclusion
Summary of preventative measures against fraud calls
Fraud calls can be a nuisance and can pose a serious threat to individuals’ financial information and personal security. However, by following a few simple preventative measures, you can greatly reduce the risk of falling victim to these scams. Here is a summary of the steps you can take to stop potential fraud calls:
1. Register your phone number: Register your phone number with the National Do Not Call Registry to reduce the number of unsolicited calls you receive.
2. Don’t share personal information: Avoid giving out personal information, such as your Social Security number or bank account details, over the phone unless you are certain of the caller’s identity.
3. Use call-blocking apps and features: Take advantage of call-blocking apps and features provided by your phone carrier or available for download to block known spam and fraud calls.
4. Beware of caller ID spoofing: Caller ID spoofing is a common tactic used by fraudsters to make a call appear as if it is coming from a legitimate source. Be cautious when receiving calls from unfamiliar numbers and avoid sharing personal information.
5. Educate yourself: Stay informed about the latest scam tactics and techniques used by fraudsters. Websites, such as the Federal Trade Commission’s Consumer Information page, provide helpful resources and updates on current scams.
Empowering individuals to protect themselves against potential fraud calls
It is crucial for individuals to be vigilant and proactive in protecting themselves against potential fraud calls. By implementing the preventative measures discussed in this article, individuals can significantly reduce the risk of falling victim to fraudsters and safeguard their personal and financial information. Remember, knowledge is key in staying one step ahead of scammers, so stay informed and share this information with your friends and family to help them protect themselves as well


